- On this page
- What is a cybersecurity (risk) assessment?
- What can I expect from this guide?
- Checklist
- The 5 main cybersecurity threats and their impact
- Why should I carry out a cybersecurity risk assessment?
- Best practice for a cybersecurity risk assessment
- How do I take control of my cybersecurity risk step by step?
- Since you made it till the end …
Through a cybersecurity risk assessment.
What is a cybersecurity (risk) assessment?
A cybersecurity (risk) assessment checks whether your IT systems are adequately protected against cyber threats. It identifies vulnerabilities and provides you with specific recommendations for improving your information security.
What can I expect from this guide?
In this guide we will provide you with valuable and practical information, namely:
- The 5 main cybersecurity threats and their impact
- Why should I carry out a cybersecurity risk assessment?
- Best practice for a cybersecurity risk assessment
- How do I take control of my cybersecurity risk step by step?
- Checklist to get you in charge
Checklist
How to assess your cybersecurity risks – step by step:
The 5 main cybersecurity threats and their impact
You just can’t be too careful – the threat is real and could even drive a company out of business. Here come the 5 main threat scenarios, explained in simple terms:
-
Ransomware and malware
With a ransomware attack, hackers gain access to an organization’s network. Their goal is to steal and/or encrypt data, destroy backups, and implement remote access. As encrypted data is useless, the hackers demand a ransom for providing the decryption key. To increase pressure, they often threaten to publish sensitive data.
Malware are malicious software programs designed to infiltrate and damage computer systems, steal sensitive data, or cause other types of harm. Difficult to detect and to remove, these programs can enter a computer, for example, via e-mail attachment, download, or infected websites.
Real-life example: Hit by a ransomware attack in February 2023, the University of Zurich had to isolate parts of its IT system, which compromised access of students and employees.
|
«The key objective is to make your business-critical systems resilient to cyber incidents and to safeguard sensitive information against data leakage.» Leo Huber |
|
-
Phishing
Phishing is the most common tactic to spread ransomware. Hackers use phishing to prompt users via e-mail to click on links, provide passwords, download files, execute macros, and install malware – which they can all exploit later. This social engineering technique can be highly targeted and personalized, with attackers gathering information about their victims from a variety of sources (e.g., social media profiles).
Real-life example: In February 2023, attackers used e-mails to spread malware at SBB, the Swiss railway company. In the process, they managed to infiltrate part of the corporate network.
-
Exploiting vulnerabilities
Vulnerabilities are flaws in a computer system – hardware or software – that weaken the overall security of the system. By exploiting them, attackers can gain access to the system, steal data and install malware enabling them to take full control, move to other systems and potentially take over the whole network.
Real-life example: In 2018, personal and financial information of 380’000 British Airways customers was stolen as an attacker injected malicious code into a website of the company.
-
Weak password
A weak password (birth date, pet name, 12345, etc.) can be easily cracked, especially by automated tools, leaving your online accounts vulnerable to attacks that may compromise your personal information. It is therefore key to choose unique passwords, i.e., consisting of a combination of letters, numbers, special characters, upper/lower case, etc. Enabling two-factor authentication (something you know, e.g., password, and something you possess, e.g., smartphone) can provide an additional layer of security.
Real-life example: The Mirai botnet was created by the attacker using default or weak credentials and infecting IoT devices (see also DDoS).
-
Distributed Denial of Service (DDoS)
A DDoS attack is an organized provoked overload triggered by the sheer number of requests, which leads to a service outage (e.g., web store). Such attacks are carried out, for example, by systems of private users that have become part of a bot network. Such a network can have tens of thousands of systems or even more. DDoS attacks disrupt operations of businesses, governments, and other organizations. The goal is often to cause financial or reputational harm, or to carry out malicious activities during the chaos of the attack.
Real-life example: In 2016, Dyn suffered three consecutive DDoS attacks bringing down much of America’s and Europe's internet.
The potential impact of a cyberattack
A successful attack can have multiple consequences ranging from the encryption and theft of sensitive data, the disruption of critical operations and the delay of service and product delivery to reputational damage and financial loss, even bankruptcy.
Even with a backup, recovery is time-consuming and expensive, taking months or even years to regain trust.
Why should I carry out a cybersecurity risk assessment?
Today, information is a valuable asset – most likely also in your organization. This is why you need to protect your data and resources. However, you can only do so if you know your cybersecurity risks. And to make it even more challenging: You have to incorporate this knowledge on all levels of your company.
The key is a top-down approach. After all, your organization’s success depends on well-informed decisions. The solution is a cybersecurity risk assessment based on such an approach. It will not only provide you with an overview of the cyber threats you are facing, but also with a list of specific countermeasures.
Best practice for a cybersecurity risk assessment
The top-down approach has shown to be the best practice. It helps you to develop a company-wide understanding of the risk scenarios. Plus, it empowers you to take decisions and implement widely accepted security controls.
These are the 2 main pillars of the top-down approach and thus of a successful cybersecurity risk assessment:
|
Flexible |
Understandable |
If you want to properly quantify your cybersecurity risk and protect your business, this is the path you should follow.
How do I take control of my cybersecurity risk step by step?
Now that we have paved the way, let’s check out the cybersecurity risk assessment step by step.
|
Step 1 |
Step 2 |
Step 3 |
Step 4 |
|
Analyze your business to keep it safe from cyberattacks |
Identify your assets – they |
Get familiar with cyber risks |
Ramp up security |
|
«By starting with business processes, you make sure not to miss important risks.» Michael Lehmann |
|
Step 1: Analyze your business to keep it safe from cyberattacks
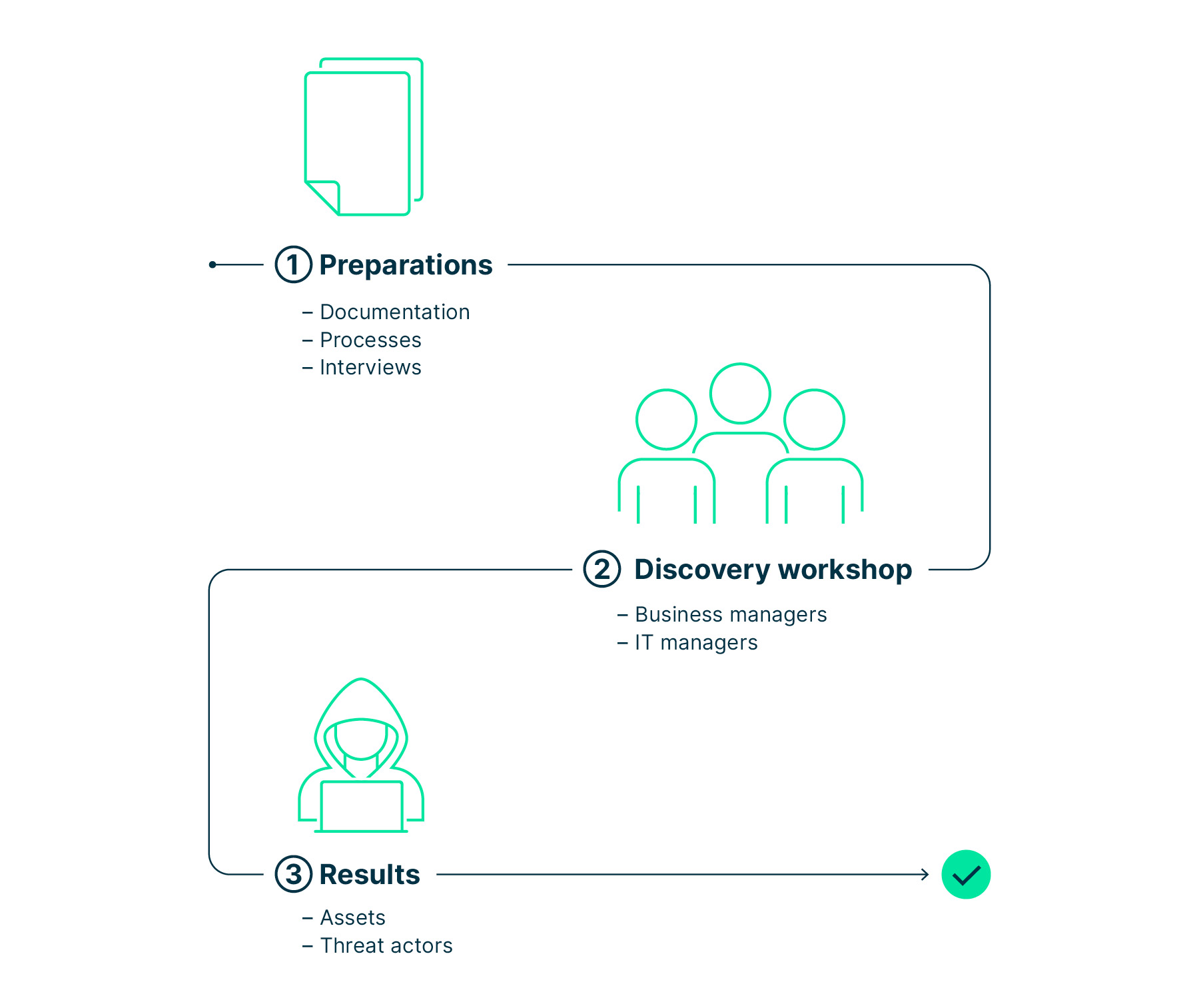
Start by analyzing your business and creating a list of the high-level assets your company needs to protect. Look into general threat scenarios, i.e., who may attack the company and why.
Identify the key stakeholders who drive the business activities you need to secure. A promising approach is to interview several responsible persons.
Also by means of interviews or ITIL, identify the most relevant digital processes. To analyze their importance, ask yourself: «What impact would it have if this process was interrupted for 1 hour, 1, 3, 10 or 30 days?»
Based on the findings, prepare all processes according to their relevance as well as a list of all potential threat actors and the associated high-level threat scenarios.
Time to get hands-on …
Run a discovery workshop. The main goal is to understand the company’s business activities and threat landscape. Model them on a high level in terms of processes. Invite management, the drivers of the business, and the drivers of digital infrastructure and operations.
In the workshop, sketch the critical processes and decide together what assets need to be protected. There are two categories of assets:
- business assets
Data, components, or functionality that is essential for your company’s mission and part of its ecosystem, such as your corporate image, contracts, and intellectual property
- security assets
Components or functionality that is particularly valuable to a potential attacker, such as patents, customer data, critical infrastructure, transactional systems, or financial data.
You are now able to define the threat actors and high-level threat scenarios.
After the completion of your business analysis, you will
- have gained an overview of your business processes,
- have a list of assets you want to protect as part of critical business processes, and
- have defined the cybersecurity threat landscape, including the threat actors and high-level threat scenarios.
Step 2: Identify your assets – they may serve as targets for attackers
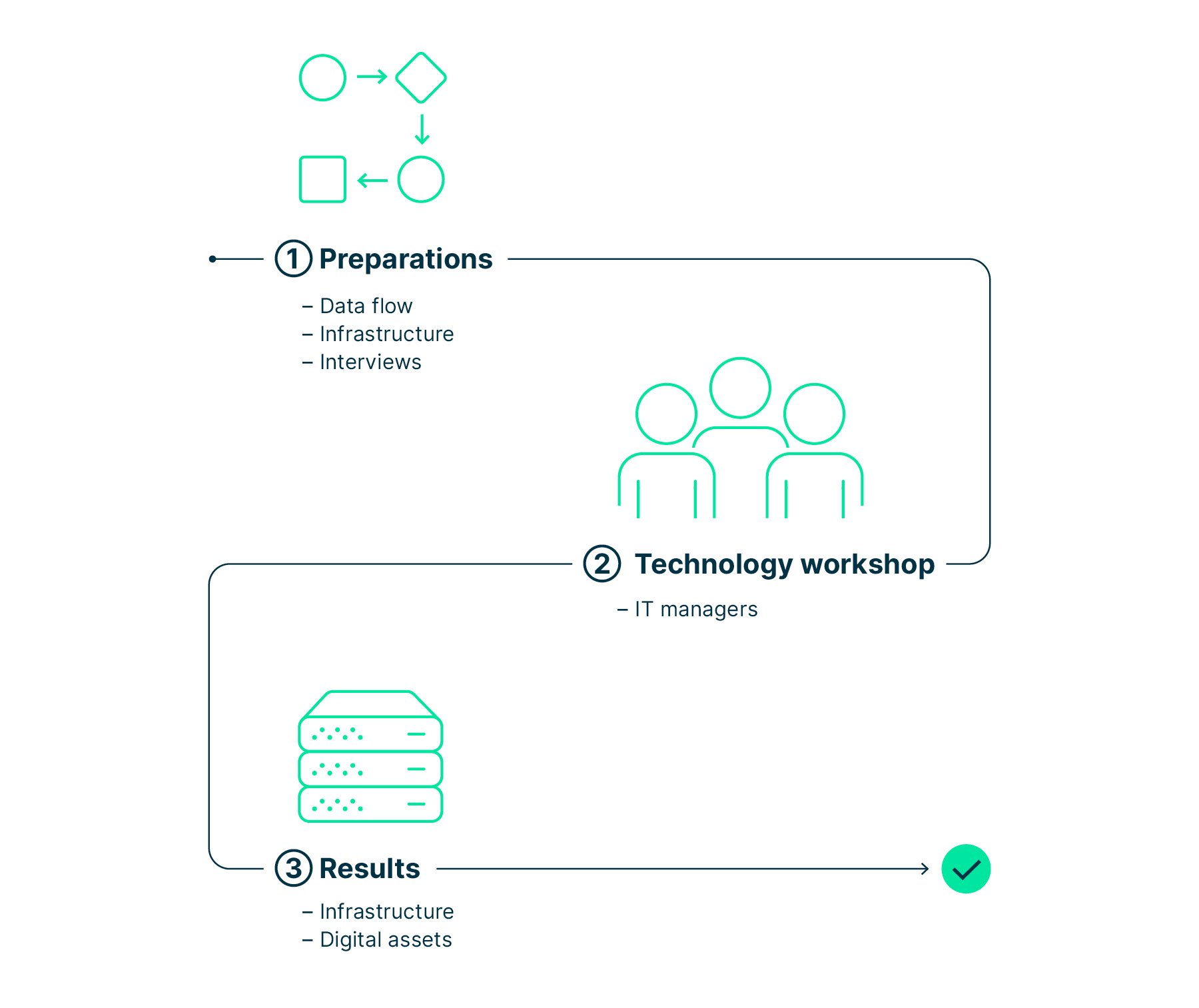
Now properly evaluate the cybersecurity threat scenarios you have identified. To do so, you must understand the digital architecture of the business and model it.
Ultimately, you want to know how critical business processes are digitalized and understand the related technology assets.
Start by collecting all available documentation on architecture and data flows. Then interview the IT managers to gain an in-depth understanding of key digital processes and related data flows.
Now you’re ready for the technology workshop. Invite the head of IT, CIO, and CISO. Together, visualize critical business processes as a digital workflow. This will allow you to identify the digital systems – potential targets – related to all business and digital assets. Plus, sketch the information flows. You will end up with the definition of the digital architecture.
Once you’ve dealt with the technological aspects, you will:
- have a list of all digital assets and data flows,
-
have transcribed all assets in terms of data (in motion, at rest, in use),
-
know your digital system architecture,
-
know the configuration of systems that are part of the architecture,
-
be able to derive the attack surface associated with the digital assets,
-
have a list of resilience and alignment requirements at hand, and
-
have a list of threats.
Step 3: Get familiar with cyber risks
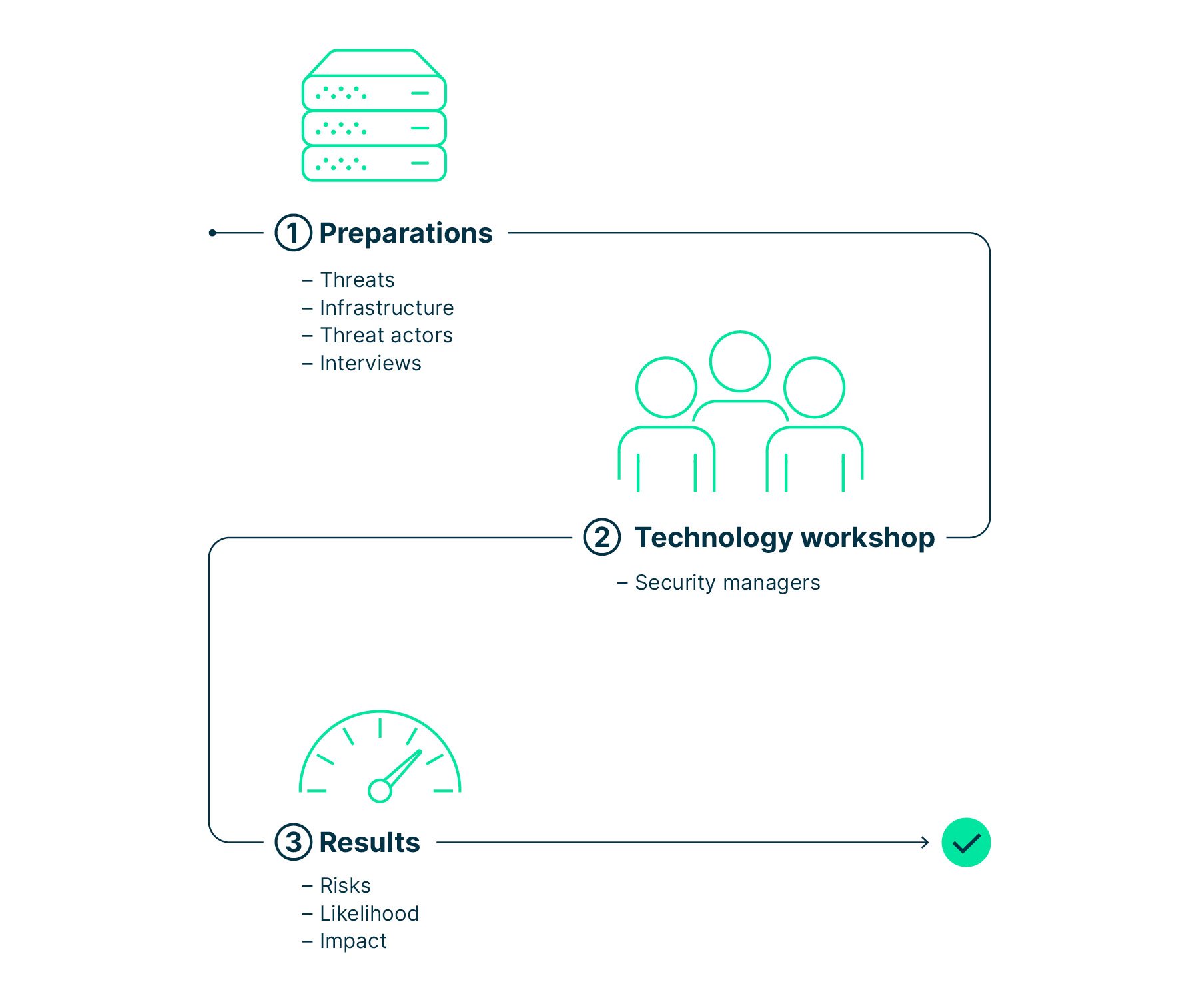
The big question here is: What is my attack surface? To find out, carefully identify and analyze the potentially accessible perimeter of your digital infrastructure.
An analysis of network diagrams, infrastructure and systems will, first, provide you with an overview, and furthermore help you to understand and quantify the cyber risks your business is facing.
Now it’s time to conduct a security workshop. Your guest list should include business, IT, and security stakeholders. As a team, identify the cyber risks based on a combination of assets, the resulting attack surface, and meaningful threat scenarios.
At the end of this step, you will
-
have gained a detailed overview of the security architecture and digital systems,
-
be able to classify the risks according to their relevance, and
-
be able to validate the list of prioritized risks with your business stakeholders.
Step 4: Ramp up security
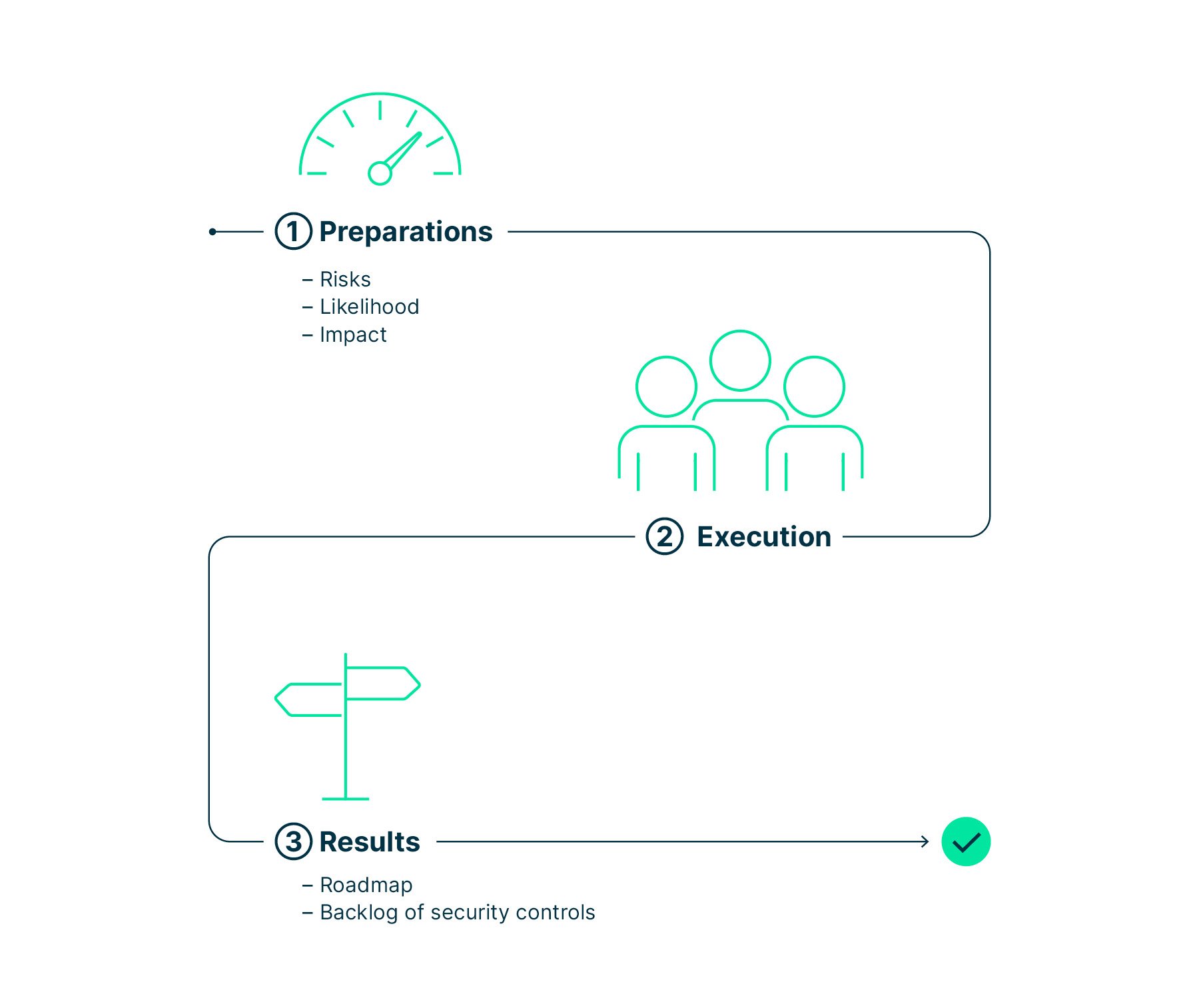
You’ve come a long way … now complete the mission. Define specific risk mitigation measures and validate them with your business stakeholders. This will enable you to create a roadmap and implement security controls in a timely manner.
Start by analyzing all identified risks in terms of probability and impact. Based on the result, roughly define mitigation measures for each risk according to best practices.
Invite business managers, IT managers, and security stakeholders to a planning workshop to coordinate the implementation of the mitigation measures.
How to tackle the challenge?
- Define security controls for each risk and calculate the residual risk,
- define the implementation budget and timeline for each control,
- validate budget requirements and other constraints per control with business stakeholders, and
- have business stakeholders accept the residual risks.
You are just one step from the finish line!
Cross it by creating a backlog with prioritized security controls and establishing an implementation plan!
Since you made it till the end …
… don’t waste any more time. Align teams throughout your company on the topic of cybersecurity: business, architecture, engineering, operations, and analysis.
The top-down approach allows for an organizational and functional alignment, putting the required digital resilience and security posture within your reach.
Select the company-wide security controls through a business lens. With business input considered first, risk management performed properly based on the top-down approach will be well accepted. This helps you achieve stronger cybersecurity defenses and more efficient security operations.
The common data sets which result from the functional security control analysis and from attack modeling are crucial to analysts, architects, and engineers. They enable tactical, strategic, operational, and architectural improvements at the same time.










