- On this page
- What does digital identity mean?
- What are the types of digital identity?
- Players in the digital identity ecosystem
- Are digital identities safe? The risks of digital identity
- Why is digital identity important? Advantages and opportunities
- The adoption of the E-ID in Switzerland and abroad
- The future of digital identity
- Quo vadis, digital identity?
We live in an information-rich and interconnected world where our ability to maintain full control over our private information is limited. Surveys show that a majority of people are highly concerned about their privacy and the lack of transparency in the digital universe. This particularly applies to digital identities.
To address these concerns, we give you the full picture on digital identities: from their definition and examples to their risks and advantages. In addition, we shed some light on the adoption of the E-ID in Switzerland and the future of digital identities.
Even better: Gain not only fact-based, but also first-hand insights from a government, technical, social, and industry perspective from our five industry experts Nathalie Gratzer, Federal Office for National Economic Supply FONES, Katrin-Cécile Ziegler, digital economist and tech journalist, Christian Heimann, Federal Office of Police fedpol, Urs Fischer, Health Info Net, and Olivier Pallière, Principal IAM Engineer with Adnovum.
What does digital identity mean?
A digital identity is the information and data that identifies an individual in the digital world. In other words: an electronic representation of an individual often used to access online services, make purchases, and interact with others on digital platforms.
A digital identity can include personal information as well as a person's online behavior.
Definition of digital identity from the experts
A digital identity can be defined as an individual’s digital presence. More precisely: a set of digitally captured attributes, such as name, date of birth, and gender combined with credentials that are linked to a unique identifier.
|
«A digital identity allows identifying a person and thus facilitates transactions in the digital world.» Nathalie Gratzer |
|
What does a digital identity consist of?
A digital identity serves as credential if:
- an individual has only one identity within a system
- an individual is aware that their information is captured
- the identity is verified and authenticated to meet government and private sector standards and to comply with regulations
- the individual can be ensured that their data is safe and accessible to them
Opposite to a paper-based ID, a digital ID (such as an E-ID) can authenticate an individual remotely over digital channels. It can track their activities and collect information, such as personal data, behavior and interactions.
To look at it from an individual’s perspective: The digital ID is similar to a person’s physical identity and personality. Therefore, individuals need to be able to decide what their digital identity is and to be in control of what they want to share.
From a more technical perspective, a digital identity is the full information that relates to a person, an organization or even a device that is used to perform online authentication.
What are the types of digital identity?
Depending on the activities a user wants to perform, they need a different type of ID. While purpose, data elements, and requirements may differ, the IDs have one thing in common: a numerical or alphanumeric code that serves as a unique identifier and thus considerably improves security.
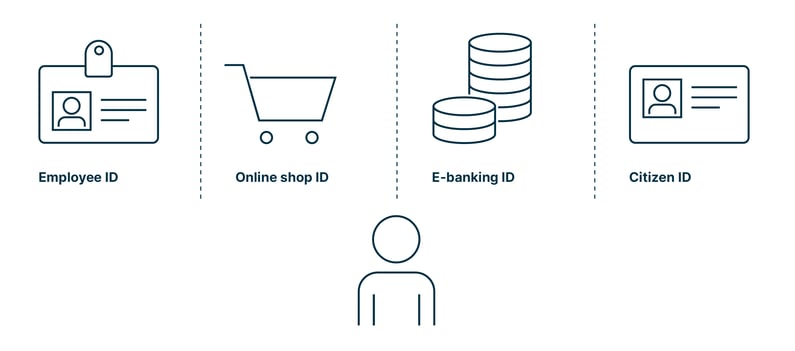
Four examples of digital IDs we all use in our daily lives:
- Employee ID
Assigned by the employer, it allows the employee to access the internal network, enter the building, or use other company resources. The employer, in turn, uses it to manage employee data, give permission to applications, monitor performance, etc.
- Online shop / Customer ID
No secure online purchase without a customer ID. While the user benefits from increased security when using a customer ID, it has multiple advantages for providers: it helps them to manage data, i.e. track customers’ transactions, preferences, or demographic information. But it also allows them to improve customer service, personalize marketing campaigns, and even to prevent fraud by detecting unusual patterns.
- E-banking ID
Also here, security is key. The e-banking ID a user needs to access online banking services usually consists of a username/password, contract number, and SMS code or QR code. Once logged in, customers can see their bank account information and make transactions, e.g. pay bills or trade securities.
- Citizen ID
Authorities provide citizens with secure access to their online offerings 24/7, enhancing public service and the interaction with their customers. Citizens are able, for example, to order official documents, thus avoiding time-consuming visits to offices. In addition, every taxpayer finds a personal identification number on the tax return they need to complete, which allows them to submit the papers electronically.
How does digital identification work today?
To use any kind of digital services, users must authenticate themselves on the provider’s website with their credentials. The procedures to register and then log in are almost as numerous as the websites. Users therefore end up with countless logins and accounts. A major nuisance.
For the sake of user experience, a high number of digital service providers allow authentication via social accounts, such as Google, Facebook, and Apple. In addition, Switzerland has launched an e-ID initiative aiming to facilitate life for citizens by providing them with an official digital ID that can be used country-wide.
Let us illustrate the catch in social account login with the help of the two popular websites Google and Galaxus:
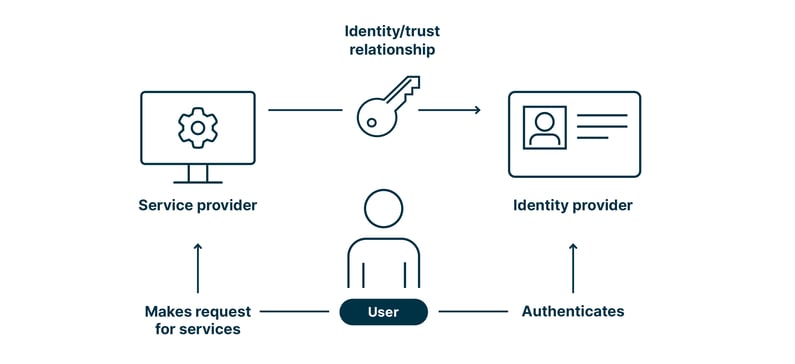
If users want to shop till they drop on Galaxus, they can either open a Galaxus account from scratch or via their existing Google account. This is possible because Google acts as identity provider (IdP) and Galaxus as service provider that trusts Google.
The advantage is obvious: By logging in via Google, users save time and have to manage only one account. One that is widely accepted in the digital universe.
No surprise, there is also a disadvantage: Google knows exactly how often users log in to Galaxus. Of course, there are already concepts that tackle this disadvantage, one of which will be presented in the section «The adoption of the E-ID in Switzerland and abroad».
Players in the digital identity ecosystem
For digital identities to work in a reliable manner and to leverage the benefits they provide, a well-balanced ecosystem is required. This ecosystem should be characterized by trust, security, and transparency. It includes the following key players:
Society
«Society» refers to the identity owners: individuals who own and control their digital identity by creating and managing their online accounts and profiles.
It may take 10 to 20 years to see whether the concept of digital identities is widely accepted by individuals and becomes a reality. One key driver in addition to security might be usability.
|
«Digital identity is all about trust. We should thus make sure to use government-issued verifiable credentials.» Olivier Pallière |
|
Government
The government agencies and industry organizations establish standards and regulations for digital identities, thus making sure they are interoperable, trustworthy, secure and ethically correct.
Tech
Tech companies provide solutions for digital identity management, such as biometric authentication systems, blockchain-based identity platforms, and identity and access management software. They make the ecosystem’s heart beat.
Businesses
Providing online services, businesses are the individuals’ counterpart. They rely on digital identities to authenticate potential buyers and provide secure access to their services, such as e-commerce or social media platforms, and financial institutions.
Identity verifiers
These are organizations that verify the authenticity and accuracy of an individual’s identity information, such as credit reporting agencies and government agencies.
Are digital identities safe? The risks of digital identity
When implementing processes in the digital world, it is vital to secure the whole digital world. In Switzerland, for example, there are state-of-the-art technologies that make it possible to create safe spaces.
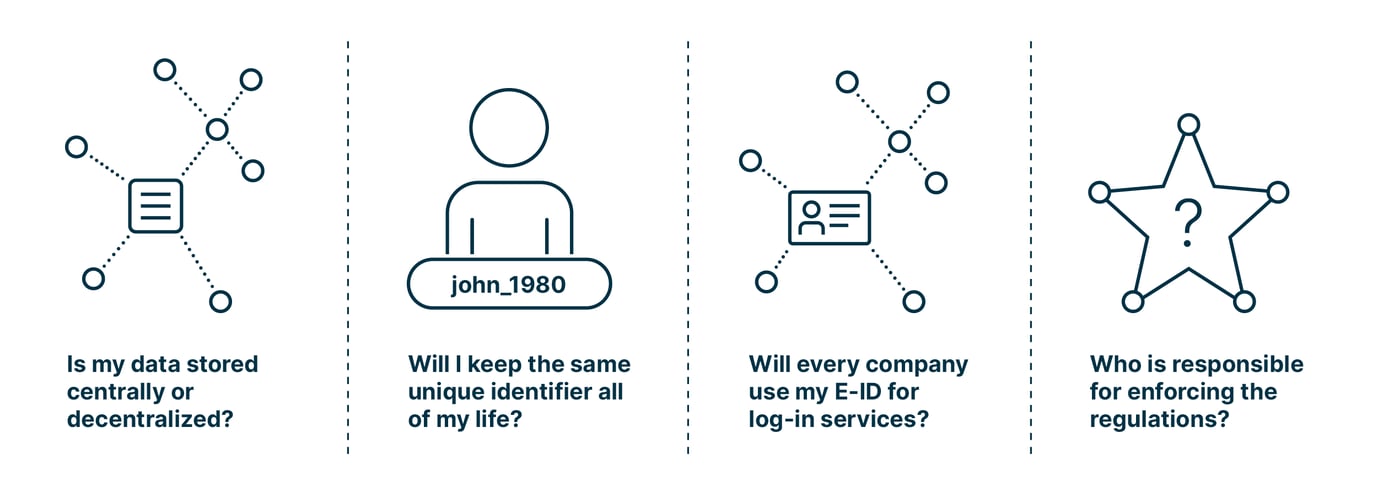
Nevertheless, digital identities come with a number of questions and challenges – all related to the loss of control:
- Is my data stored centrally or decentralized?
In case of central storage, digital identities might be an attractive target for attackers. As a private person, do I need to be concerned about paying a ransom? - Will I keep the same unique identifier all of my life?
The European Union recently voted against a life-long unique identifer as it is considered a loss of anonymity. - Will every company use my digital identity for log-in services?
It is a completely different story whether an e-commerce platform on which you buy a bottle of shampoo asks for my credentials or a financial or a medical institution, which manages sensitive data and has higher security requirements. - Who is responsible for enforcing the regulations?
Is it my responsibility to only share the information my counterpart really needs? Or the service provider’s? Or the government’s?
Cyber hacks
No surprise: Security is one of the major challenges when it comes to digital identies. This is reflected by the thousands of cybersecurity incidents reported every year. In 2022, for example, a well-known password manager lost the data of more than 25 million users, including encrypted password vaults.
As there is no way out of digital identities, let us face the risks associated with using them:
Risks of USING the digital identity
As a matter of fact, risk or rather reducing risk is one of the main drivers of the adoption of digital identities besides saving money.
|
«It is important to distinguish between the real risk of using an identity and other cyber risks.» Urs Fischer |
|
The risk of security breaches has existed since the World Wide Web was released in the 1990ies. Yet, digital identities are particularly sensitive: If they are affected by a security breach, an individual may suffer a personal attack – comparable to one in real life.
Some of the risks individuals should be aware of when using their digital identity:
- Identity theft
An attacker may gain access to personal information or even take over an individual’s digital identity, leading to e.g. financial fraud. - Privacy
Digital identities require users to share personal information, which raises privacy concerns. Individuals may not always be aware of how their information is used, who has access to it, and how it is protected. - Inaccurate information
Sometimes a digital identity can be based on inaccurate or incomplete information, which then leads to problems with identity verification or access to services. - Cyberbullying
Digital identities can be used for cyberbullying and harassment. This may be especially harmful for young people, as they are more vulnerable to online abuse.
The upcoming Swiss E-ID will mitigate or remove some of the risks, as it is based on the decentral Self-Sovereign Identity concept.
Creating awareness for digital identity (aka educating the masses)
While a digital identity is a convenient means of authentication for individuals, it also provides a wealth of information to service providers, including a person’s thoughts, needs and actions.
Yes, this is creepy.
In addition to creating safe spaces, it is therefore imperative to help individuals understand how sensitive the information contained in a digital identity is. They should understand what action is performed in which moment and what evidence of this is in a system.
Another fact individuals need to be aware of: It is hard to align our requirements – being in control of our data – with our expectations – having a third party validate our identity.
In Switzerland, the discussion about digital identities is currently shifting from the technical to the political area with the government working on an E-ID Act. Chances are that the political discussion will help to reach a broader audience and result in a decent level of digital literacy of citizens.
Why is digital identity important? Advantages and opportunities
A digital identity enables individuals to engage in online transactions and communications with confidence and trust. It comes with many benefits for all the players in the ecosystem:
Convenience
With a digital identity, online services and information are only a few clicks away. Authentication is done in no time. Personal information, such as credit card details, has to be entered only once when online shopping.
Applied to B2B, the concept of digital identity might increase process efficiency and thus solve instead of creating problems.
A trusted digital identity
- can be used for onboarding instead of video identification
- can receive secret data
- can help to minimize data stored in the system by providing information
Economic benefit
As experience shows, the economy benefits the most from the use of digital identities. Scandinavian countries – so-called digital first societies – increased their GDP by 3–13%. The potential for Switzerland is also considered significant.
Semantics
With a digital identity based on a privacy by design concept, it is possible to bring semantics to deep data exchange in a harmonized way between different actors. For example: If an individual needs to provide their diploma for a job application, a company cannot just filter the person out due to a bad grade.
Privacy
Using a digital identity, individuals have the chance to regain control of the information they want to share, e.g. their full identity, specific details or attributes. A digital identity can also offer enhanced privacy by allowing an individual to control how their personal information is used and shared and to revoke access to information at any time.
Process efficiency
A digital identity is a means of establishing trust in real digital processes by enabling secure, convenient, and efficient transactions and communications online. This ultimately leads to more efficient processes.
A real-life example: When an individual checks into a hospital, they have to answer countless questions – multiple times. Who are you? What's the name of your insurer? What exactly happened? If all this information was digitalized and even centralized, it would be a huge time-saver for everyone.
The adoption of the E-ID in Switzerland and abroad
While the adoption of a government-issued digital identity (E-ID) will facilitate the lives of individuals and service providers alike and thus boost the economy, the legal enactment is time-consuming, acceptance by citizens not guaranteed.
Countries with a government-issued digital identity include Estonia, Ghana, China, and the Philippines. In 2021, the European Commission put forward the eIDAS 2.0 proposal, aiming to enable at least 80% of people to use a digital identity to access key public services across EU borders by 2030.
In the US, there have been discussions and proposals for the creation of a national digital identity system, which would provide a secure and standardized way for individuals to authenticate themselves online and access various services. Examples of proposals include the National Strategy for Trusted Identities in Cyberspace (NSTIC) and the Digital Identity Act of 2019.
E-ID: Adoption as a recognized identification
If the E-ID should become a success, the issuers need to
- ensure digital literacy of individuals
Generally, a digital identity improves the users’ security. However, they need to be aware that passwords like «hello» or «1234» and uploading confidential documents to social platforms eliminate this benefit. - give them a real choice in which case they want to use it
Just as a person can choose whether they want to buy a bottle of wine themselves or send a friend to get one, they should be free to choose whether they want to use the E-ID.
E-ID adoption in Switzerland
After the rejection of the E-ID Act in March 2021, the Swiss Federal government continued to work at full speed on a new proposal. The first results were published in a discussion paper in September 2022.
The revised Federal Act on Data Protection (rev FADP) – aiming to better protect Swiss citizens data – that was enacted in Switzerland in September 2023 may lay the grounds for the adoption of the E-ID.
One key factor are verifiable credentials. Already today, a verifier acts as a third party who receives and collects data and has the necessary technical legal basis to protect the person the data belongs to.
The E-ID should be a unique credential with which individuals prove their identity. In the medium term, people should become aware of the advantages and of how to use verifiable credentials. Meaning: they can use them to request a service, not just to prove their identity like with a unique credential. For this to happen, it is necessary to think in terms of an ecosystem of digital credentials and to set up an appropriate infrastructure. The E-ID is the stepping point for this transition.
E-ID adoption in the EU
The European Union plans to go one step further than Switzerland. They are working on a regulation that shall obligate all the verifiers in the system to know exactly what attribute they will ask when, where, and for what reason.
|
«In Germany, only 10% of the citizens use the government-issued E-ID due to poor APIs and lack of applications.» Katrin-Cécile Ziegler |
|
Germany introduced an E-ID ten years ago. However, only 10% of the citizens use it – discouraged by poor APIs and a lack of applications. For example, a person with a walking disability cannot apply for a parking permit online. The person has to go to the responsible office, which is a major, even impossible effort.
Germans currently use mainly identification methods provided by the private sector, such as Google, Apple, or Facebook accounts – which can be created with two clicks.
The future of digital identity
Let’s face it: The future is here to stay. The solution is a decentralized government-issued identity that provides the basis for real digitalization.
Switzerland is hoping to start building an ecosystem with a high number of players by 2025/26. Officials are aware that in every technical concept there are security issues or open legal or technical questions. Nevertheless, they want to move forward in a pragmatic way, hopefully encouraging European countries to follow.
|
«We can be the digital identity pioneers, and maybe other countries will join us.» Christian Heimann |
|
For the ecosystem to be successful, it will be key to create trust spaces, trust rooms, and data rooms. These serve to securely collaborate within B2B and also B2C. In such a space, individuals will more likely be willing to exchange sensitive information with their counterparts, be it financial or medical data. As a result, efficiency increases for all the parties involved.
Digitalization goes far beyond scanning a piece of paper and converting it into a PDF. It is about introducing new processes rather than transferring physical processes 1:1 to the digital world.
Self-Sovereign Identity (SSI)
SSI brings distinctive advantages for individuals:
- They have full control of their personal data which is stored in their mobile wallets.
- Using their wallet, they keep their credentials and login activities confidential.
- They are able to disclose information in a targeted manner (concept of «selective disclosure»).
Let us dive into the real world. If a young person wants to buy alcohol, he/she has to show a piece of ID – disclosing name, age, maybe address.
In the digital world, individuals benefit from zero knowledge proofs (ZKP) with SSI. ZKP allows a holder to answer a yes-or-no question without revealing the data. In other words: The person buying alcohol can just give proof that he/she is over 18 without revealing his birthday.
SSI in combination with smartphone security is a huge gain for the data privacy of users. It solves core privacy problems existing in centralized and federated identity models.
Building an ecosystem
To promote the wide use of digital identities, a functioning ecosystem is necessary: a shared infrastructure, with jointly defined rules and many possibilities for the most diverse actors in the system.
Ideally, the ecosystem has open and standardized interfaces, has coordinated governance, does not maintain bureaucratic, inhibiting rules, and allows practical, automatable updating of digital identity data.
Individuals may be convinced to join the ecosystem by
- providing convenient, transparent and understandable interactions in the ecosystem
- ensuring trust in the system, the participants and the value of the data
- allowing for use free of charge and without requiring any additional devices
- keeping the entry hurdles low
In sensitive areas, such as healthcare, personal aspects and professional aspects are heavily mixed, for example when a doctor has to prove his/her ability to do something. This reflects the use of digital identities in a professional context.
In B2B, there is a high chance to establish ecosystems that enable the use or increased use of digital identities. While proving the identity is not a day-to-day case, processes that rely on approved identities are. It’s the old chicken-and-egg story.
The federal government has illustrated the potential of ecosystems by means of three levels of ambition: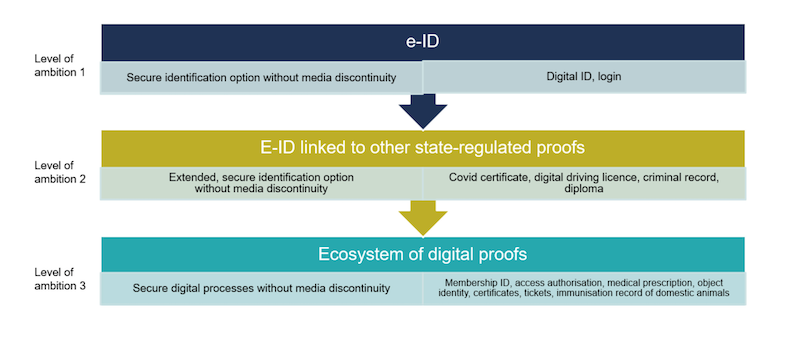
E-ID as a way to improve public services
A government-issued E-ID has the potential to improve public services in multiple ways:
Accessibility: An E-ID allows citizens to use public services online, reducing the need to visit government offices in person. This makes public services more accessible to people with mobility issues or living in remote areas.
Efficiency: Thanks to their E-ID, citizens can authenticate themselves quickly and easily, which reduces the time and resources needed to verify their identity manually.
Security: An E-ID comes with a higher level of security than traditional identification methods, such as physical documents or passwords. This helps to prevent fraud and protect sensitive personal information.
Cost-effectiveness: The use of E-IDs reduces the cost of administering public services, as digital processes minimize the need for physical documents and manual verification processes.
Digital wallets
Digital wallets are a success factor for the acceptance of the E-ID. They give individuals full control of their personal data and keep their credentials and login activities confidential.
According to the Swiss law, an individual should have the choice where to store his E-ID once the identity is verified in an onboarding process: the government, the private, or a third-party wallet.
Whether the E-ID wallet will only be available on the mobile or also web-based, has not been defined in the law proposal. The main goal of the government is to make sure that citizens can store, protect, and present their verifiable credentials in a secure and state-approved way. In a first version, this feature will be designed for mobile.
Social media and nickname verification
Authentication via social accounts, such as Google, Facebook, and Apple, is a standard today and very convenient. To protect their privacy and personal information while interacting with others, many people use nicknames for their profiles.
Could the government-issued E-ID act as a trust anchor for a person’s pseudonym on the internet? Providing this option might help to grow the ecosystem and to prevent misinformation on the web – which is a major problem considering the situation on social media.
In brief: The main purpose of the E-ID is to identify someone, not to make a «know your customer» process with easy identification, such as face-to-face or video identification, available.
A service provider wants to know if the user logging in is a real person and if this person has logged in before.
Quo vadis, digital identity?
Currently, a large number of people is still skeptical about digital identity. This is comprehensible considering the risks such as identity theft or lack of privacy. However, going forward it is crucial to understand that digital identity does not equal digital identity:
- A digital identity as we all know it today is a common identity, such as a Google, Microsoft, or Facebook ID, we use online.
- A decentralized identity, also referred to as Self-Sovereign Identity (SSI), uses digital identifiers and verifiable credentials that are self-owned, independent, and enable trusted data exchange.
- A government-issued identity, such as the Swiss E-ID, will be based on SSI and also the Swiss E-ID act, thus providing maximum trust and security.
The upcoming Swiss E-ID is a step in the right direction at the right time, as it will combine the benefits of a decentralized identity with the user benefits, such as trust, privacy, and security.
FAQ
-
What are examples of digital identity?
The currently most common types of digital ID are the employer ID, which grants access to company premises, resources and assets, the Online shop ID, which streamlines and secures your dealings with online storefronts, e-banking IDs, which use advanced security measures for your financial operations, and finally government-issued IDs, which give you access to government services.
-
What is a digital identification system?
A digital identification system serves the purposes of identifying and authenticating users, devices, and organizations in their online dealings. This is achieved through software and hardware that collects, stores, and verifies such personal information as name, date of birth, and biometric data.
-
What are the methods of digital identification?
The username and password remain the most common method of digital identification, along with technical measures that identify your device, such as its IP address and cookies. Examples of methods that provide more security are two-factor authentication (2FA), biometric authentication, single sign-on (SSO), OAuth, and self-sovereign identity with digital wallets.
-
What is digital identity verification?
Digital identity verification is the process of identifying a person or organization by means of various technologies and verifying that the presented digital identity belongs to the entity presenting it. This process is of vital importance to ensure secure online activities and prevent adverse occurrences such as fraud and identity theft.
-
What is digital identity used for?
Digital identities are employed for a wide range of purposes and benefits, ranging from the authentication and authorization of users for access to information and resources, to facilitating e-commerce and creating a personalized experience for online users. Furthermore, digital identities play a crucial role in cybersecurity measures and compliance with official data protection regulations.
-
What types of information make up your digital identity?
On the one hand, a digital identity is composed of your personally identified data, such as your name, date of birth, address, e-mail address, etc. The other part of your digital identity is your behavioral data, i.e., the information on your online activities, to include your browser history, search queries, social media interactions, and purchase history.










