As organizations navigate the complexities of cybersecurity, a looming challenge emerges from within – the insider cybersecurity threat. With technological advances, the methods employed by malicious insiders are increasingly becoming more sophisticated. According to a Cybersecurity Insiders’ report, 74% of companies are at least moderately vulnerable to insider threats. It also revealed that the average cost of an insider threat incident in 2023 is $15.38 million1. While we often hear about external threats like hackers and malware, it is equally important to focus on insider security threats. These threats may arise from current or former employees, contractors, or business partners with access to sensitive information within your organization. In this article, we will delve into the world of insider security threats and outline a holistic approach to tackle them effectively.
Understanding Insider Cybersecurity Threats
Generative artificial intelligence (AI) plays a pivotal role in understanding and mitigating insider threats. With the ability to analyze vast datasets and identify patterns, generative AI can enhance anomaly detection systems, making it easier to pinpoint unusual behavior indicative of a potential insider threat.
Types of Insider Cybersecurity Threats
Insider cybersecurity threats can be categorized into three primary types:
- Negligent Insiders: Negligent insiders are employees who inadvertently compromise security due to carelessness or lack of awareness. They may, for example, fall victim to phishing attacks, share sensitive information unintentionally, or use weak passwords.
- Malicious Insiders: Malicious insiders, on the other hand, have harmful intentions. These individuals may exploit their authorized access to steal data, sabotage systems, or disrupt operations deliberately. Their motives could range from personal gain to revenge.
- Compromised Insiders: Compromised insiders are employees whose credentials or access rights have been compromised by external attackers. Cybercriminals may use these insiders as unknowing pawns to carry out their malicious activities.
Common Motivations Behind Insider Cybersecurity Threats
Understanding the motivations behind insider cybersecurity threats is crucial for effective prevention. Motivations can range from financial gain and revenge to ideology or espionage. Financially motivated insiders may seek to steal intellectual property, trade secrets, or sensitive financial information. Unhappy employees might retaliate against perceived injustices, while ideologically motivated individuals may target organizations based on political or social beliefs.
Importance of Addressing Insider Cybersecurity Threats
Insider threat defense offers several benefits beyond just security enhancements. These benefits can have a positive impact on various aspects of an organization's operations. Some of the key benefits of insider threat defense include:
- Data Protection: Protecting sensitive data from insider threats helps maintain the trust of customers and partners, as well as safeguarding your organization's reputation.
- Legal Compliance: Compliance with data protection regulations such as GDPR, HIPAA, or CCPA requires organizations to have measures in place to address insider threats.
- Business Continuity: Insider threats can disrupt operations, leading to downtime and financial losses. Mitigating these threats ensures business continuity.
- Cost Savings: Preventing insider threats is more cost-effective than dealing with the aftermath of a security breach, including legal fees, fines, and reputation repair.
Adopting a Holistic Approach for Insider Risk Management
To effectively handle insider cybersecurity threats, organizations should adopt a holistic approach that includes the following components:
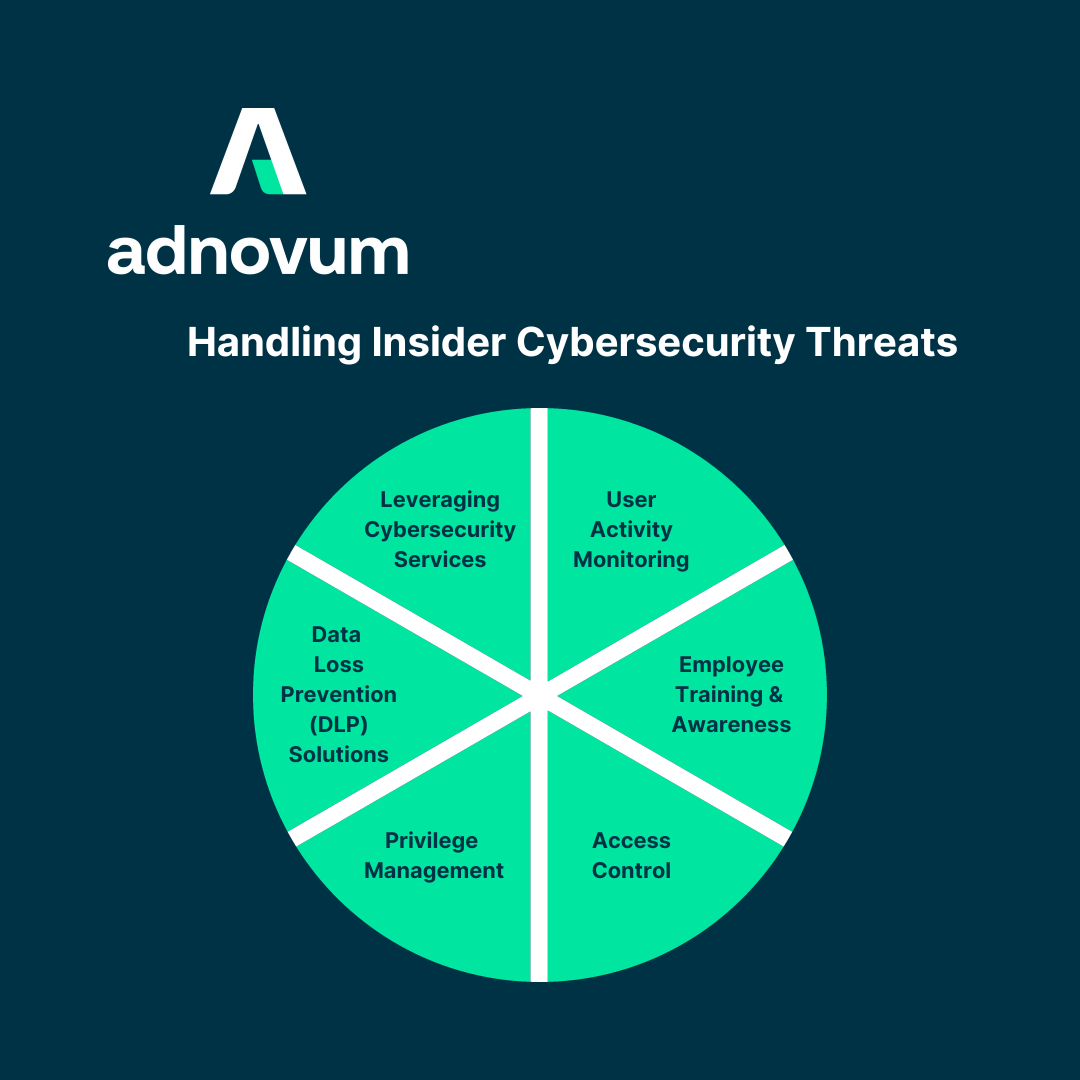
- User Activity Monitoring: AI-powered tools continuously monitor and analyze user activities, flagging suspicious actions such as unauthorized access or data exfiltration. This proactive monitoring helps organizations respond in real-time, minimizing potential damage.
- Employee Training and Awareness: Invest in cybersecurity training and awareness programs to educate employees about potential threats and best practices. Regular training can help employees recognize and report suspicious activities.
- Access Control: Implement strict access controls that limit employees' access to only the data and systems necessary for their roles. Generative AI can aid in refining access control policies by continuously analyzing data access patterns and suggesting adjustments based on evolving organizational needs.
- Privilege Management: Employ the principle of least privilege (PoLP) to ensure that employees have the minimum level of access required to perform their job functions. This reduces the potential damage caused by insiders with malicious intent.
- Data Loss Prevention (DLP) Solutions: Deploy DLP solutions that monitor and prevent unauthorized data transfers or leaks. These tools can detect and block sensitive data from leaving the organization without authorization.
- Leveraging Cybersecurity Services: Consider partnering with cybersecurity service providers who specialize in insider threat detection and mitigation. These experts can help identify vulnerabilities and develop tailored solutions. In addition, consider undergoing a cybersecurity assessment to identify key areas for improvement.
In conclusion, insider cybersecurity threats are a significant concern for organizations, but with a well-rounded approach in place, they can be effectively managed and mitigated. By understanding the types and motivations behind insider cybersecurity threats, emphasizing employee training, implementing access controls, managing privileges, and leveraging cybersecurity consulting services, businesses can fortify their defenses against this often-overlooked threat vector. Get in touch with Adnovum's team of cybersecurity professionals today to strengthen your defenses against insider cybersecurity threats.
📩 Sign up for our newsletter and gain access to exclusive executive insights and event invitations.
Reference:





