Businesses are no longer passively responding to cybersecurity issues but are adopting a proactive approach. As digital infrastructure becomes the lifeline of every operation, organizations can no longer afford to wait for breaches to happen. The stakes are simply too high. In 2023, the average cost of a data breach was 4.45 million USD (Statista, 2023)1 . To adapt to this reality, cyber risk management is evolving from a defensive measure to a strategic offensive, allowing organizations to strengthen their defenses and stay ahead of evolving threats. This article delves into the significance of cyber risk management, unraveling the crucial steps, considerations, and practical tips essential for fortifying organizations against an ever-adaptive array of cyber threats.
Understanding Cyber Risk Management
At its core, cyber risk management is the process of identifying, assessing and mitigating potential risks to an organization's critical IT assets. These assets encompass data, systems and networks, each playing a pivotal role in the seamless functioning of modern businesses. The objective of cyber risk management is not merely to prevent cyberattacks but to manage the risk associated with potential breaches effectively.
Why Cyber Risk Management is Important and Complex
Fortune 500 companies face a staggering financial threat from cyberattacks, with potential losses exceeding $1.5 trillion annually. This represents an alarming 11% hit to their yearly turnover, a significant jump from $864 billion just two years ago (Siemen, 2023)2. In light of this escalating threat, effective cyber risk management is no longer optional; it's essential, ensuring:
- Data security: Protects sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction.
- Business continuity: Minimizes disruptions caused by cyberattacks, ensuring the smooth functioning of critical systems and operations.
- Operational efficiency: Minimizes downtime, cuts costs and boosts productivity and competitiveness .
- Brand reputation: Protects the organization's image and fosters trust with customers, partners, and stakeholders.

Despite its importance, cyber risk management is not without its challenges. Here are some key factors that contribute to the dynamic nature of cyber threats:
-
Technology Advancement: Rapid tech evolution, including cloud computing, AI, and IoT, introduces opportunities and challenges, creating new attack vectors for cybercriminals.
-
Human Factor: The human element is often the weakest link, as actions like using weak passwords or clicking on malicious links can introduce risks, making employees, customers, and third parties unintentional vulnerabilities.
-
Motivation and Capability: Cyber threat actors, from hackers to nation-states, vary in motivations and capabilities, influencing objectives from data theft to physical damage or shaping public opinion and political agendas.
Key Steps in Cyber Risk Management Process
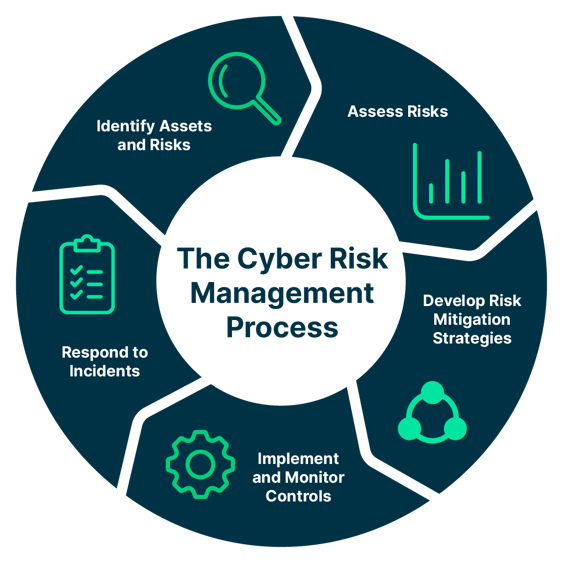
1. Identify Assets and Risks
2. Assess Risks
3. Develop Risk Mitigation Strategies
4. Implement and Monitor Controls
5. Respond to Incidents
Key Considerations for Effective Cyber Risk Management
Align Cyber Risk Management with Business Goals
Modern cyber risk management is business-driven. It's no longer just about protecting servers; it's about safeguarding the heart of your organization: your ability to achieve goals. By integrating cyber strategies with your broader vision, you build a proactive shield that empowers growth, innovation, and customer trust.
Imagine securely launching digital products without data breaches or expanding into new markets with resilient cyber defenses. This alignment empowers collaboration, uniting the boardroom, IT, operations, and every business unit. Shared responsibility, woven into governance frameworks, fortifies your organization, allowing fearless pursuit of ambitious goals amidst the cyber landscape.
Build a Culture of Cybersecurity
An organization is only as secure as its weakest link, and often, that weak link is human. To truly bolster cyber defense, we must move beyond technical solutions and cultivate a culture of security awareness and accountability, where everyone plays a vital role in safeguarding our digital assets.
- Focus on employee training and awareness programs: Regularly train employees on best practices such as password hygiene, phishing awareness, secure browsing, and data protection. Create engaging learning experiences with gamified modules, simulations, and role-playing exercises. Customize programs to address specific risks and vulnerabilities linked to various roles in your organization.
- Promote open communication and the reporting of suspicious activity: Establishing a secure workplace that fosters open communication can empower employees to report any concerns without fear. Facilitate ongoing dialogues on cybersecurity threats, emphasizing the significance of vigilance. Empowering managers through training to exemplify secure practices ensures they promptly and effectively address any security issues that may arise.
- Showcase your commitment to a secure cyber environment: Embedding cybersecurity within the company's culture and brand essence is pivotal. Executives play a central role by ardently advocating for cybersecurity, showcasing dedication through active involvement. Implement layered security measures, perform routine penetration testing, and ensure prompt system updates to fortify against evolving threats.
Embrace Continuous Improvement
Cyber adversaries evolve constantly, demanding dynamic responses. Static defenses are inadequate; we must embrace continuous evolution in cyber risk management.
Regularly update strategies, policies, and procedures, treating them like software patches to close gaps exposed by incidents and audits. Learn from these experiences to fortify defenses.
Innovation becomes our sword and shield. Harness AI and machine learning to predict and counter emerging threats. Explore blockchain for secure data sharing and transparency, unlocking untapped potential in your cybersecurity arsenal.
Practical Tips for Implementing Cyber Risk Management
To implement cyber risk management effectively and efficiently, organizations can follow these practical tips:
- Conduct regular vulnerability assessments and penetration tests, prioritizing threats and testing security controls' resilience.
- Continuously monitor IT systems and networks with monitoring tools and log management solutions, promptly responding to potential threats. Regularly update risk management programs to adapt to evolving challenges.
- Enforce strong password policies and access controls, adhering to the principle of least privilege for authorized users.
- Implement data encryption and backups to safeguard data confidentiality, integrity, and availability, ensuring recovery in case of loss or corruption.
- Utilize security awareness training and phishing simulations to educate and test employees, customers, and third parties on cybersecurity best practices.
- Consider external cybersecurity consulting or managed security services for additional expertise.
- Establish a robust incident response plan, equipping teams to handle diverse cyber incidents, and document the necessary steps, actions, and resources.
Conclusion
Cyber risk management is a critical component of modern organizational cybersecurity strategy. The dynamic nature of cyber threats requires a proactive and continuous approach to identify, assess and mitigate risks effectively. By aligning cyber risk management with organizational goals, fostering a culture of cybersecurity and embracing continuous improvement, you can build a highly resilient organization that can withstand even the most sophisticated cyberattacks, protecting your valuable assets. Implementing practical tips, such as regular assessments, strong access controls, encryption and a robust incident response plan, further strengthens the overall cybersecurity posture.
Adnovum goes beyond bolstering cybersecurity by offering flexible solutions tailored to your needs, spanning cybersecurity services, IAM consulting, IT governance tools and digital transformation expertise. Explore more of our cyber security consulting services for how we can add value to your business.







