Today’s interconnected world has led to an increase in ransomware attacks, impacting a wide range of targets. The victims might be anybody, from a single individual to a large corporation or even a whole municipality. By 2031, ransomware will cost victims $265 billion annually, and it will attack a business, consumer, or device every 2 seconds (Cybersecurity Ventures, 2023)1. Any entity without adequate cybersecurity measures is vulnerable to ransomware attacks.
This article will explain how ransomware may get into a company's network and why it's important for companies to protect themselves from this threat. The article continues by providing effective ransomware defensive strategies to protect businesses.
How do ransomware attacks happen?
In a ransomware attack, the attacker gains access to a computer system or network and encrypts the files or locks the user out, rendering the files inaccessible to the victim until the ransom is paid.
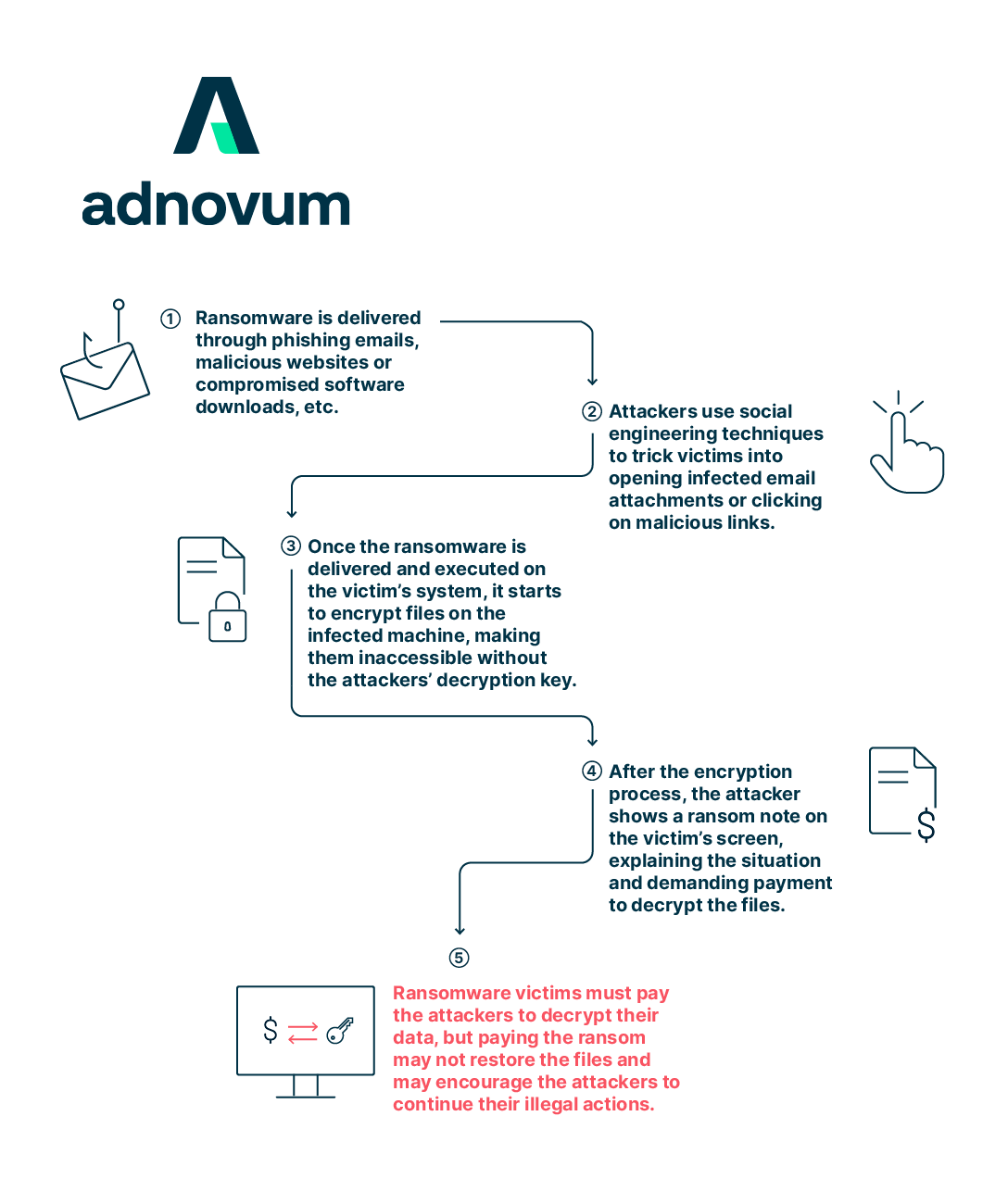
To defend themselves, businesses should have a firm grasp of how ransomware attacks function and the tactics that cybercriminals use. The following are common approaches used by ransomware hackers to compromise a system:
- Phishing Emails: As a means of infiltrating a target's network, hackers employ phishing emails that seem official but really include malware. Users are infected with ransomware as soon as they open the malicious attachment or click on the link inside the email.
- Malicious Websites: Exploit kits placed on malicious websites may take advantage of security gaps in browsers or plugins to secretly install ransomware on a victim's computer.
- Exploiting Software Vulnerabilities: Web applications, server software, and other network services are all potential entry points for attackers to seize control of your system and implement ransomware.
- Social Engineering: Attackers may impersonate legitimate entities in order to deceive employees into disclosing confidential information or allowing access.
- Insider Threats: Employees with bad intentions might install ransomware or help hackers get access to a system.
The impacts of ransomware attacks on organizations
Operational disruption, financial losses, brand injury, and the potential for legal and regulatory action are just some of the many negative impacts on businesses as a result of ransomware attacks.
- Financial losses: Losses may be substantial, including ransom payments as well as the expense of conducting an investigation, recovering systems and data, introducing cybersecurity measures, and perhaps even hiring legal and public relations counsel.
- Operational disruption: Systems and networks may be taken offline or rendered unusable, leading to downtime and productivity losses. In some cases, organizations have had to halt their operations entirely until the situation is resolved, resulting in further financial impact.
- Reputational damage: Ransomware attacks may do harm to a company's reputation if sensitive information, such as that of customers or employees, is compromised. Trust is eroded and long-term ramifications may be seen when an assault is made public or when it is perceived that an organization fails to appropriately safeguard sensitive information.
- Legal and regulatory consequences: If sensitive information is compromised in a ransomware attack, the impacted organization may be subject to legal and regulatory requirements. Organizations may be subject to fines or legal action for failing to adequately protect customer data or violating data protection laws.
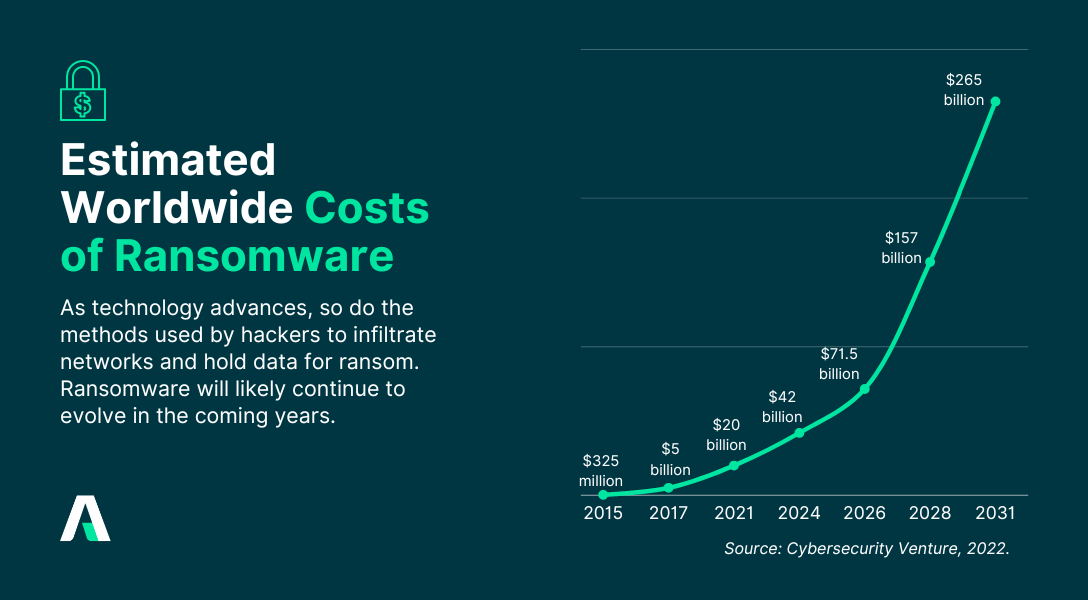
The seriousness of ransomware attacks makes it critical for businesses and individuals to take preventative measures, such as performing regular data backups, updating all software and systems, implementing stringent cybersecurity measures or consulting with an IT security service provider.
Effective cybersecurity measures to protect businesses against ransomware attacks
The probability of a devastating ransomware attack can be mitigated by using proactive cybersecurity measures. These could help detect, eliminate, and minimize the impact of ransomware. The following are some effective cybersecurity procedures that businesses can consider:
1. Regular Software Updates and Patch Management:
By maintaining vigilance and swiftly implementing updates and patches, businesses may greatly lessen their chances of falling prey to ransomware attacks. Software updates and patch management should be implemented across all systems and devices within an organization, including servers, workstations, laptops, mobile devices, and network infrastructure.
Moreover, organizations should think about using automated patch management tools to streamline the process and ensure that fixes are routinely implemented.
2. Regular Vulnerability Assessments and Penetration Testing
Risk-based prioritization and remediation of vulnerabilities are made possible by the information gleaned through vulnerability assessments and penetration testing. The findings from these assessments can also raise awareness of security best practices within the organization, thus driving improvements in system hardening, secure configurations, and user awareness, creating a more robust security posture against ransomware.
Organizations can keep one step ahead of evolving threats by doing vulnerability assessments and penetration testing on a regular basis. Considering the fact that hackers are continually finding and exploiting new vulnerabilities and attack methodologies, this is more crucial than ever.
3. Employee Training and Awareness
When employees are well-equipped with knowledge about cybersecurity, common attack vectors, and best practices, organizations can significantly reduce the likelihood of successful ransomware incidents.
Employees can be educated about ransomware attacks via a variety of awareness trainings, such as phishing awareness, social engineering awareness, password hygiene, safe online surfing, etc. It's important for organizations to tailor their training programs to address their unique cybersecurity demands and foster a strong security culture among employees.
4. Implement robust identity and access management solutions
IAM solutions play a crucial role in controlling user access to critical systems and data, adding an additional layer of protection against ransomware and other cyber threats. The following are some of the ways in which IAM solutions may help lower the chance of successful attacks and the potential consequences should an event occur:
- Unauthorized entry prevention: using the principle of least privilege, multi-factor authentication (MFA), and strong password policies to reduce the risk of unauthorized entry
- Containment of ransomware spread: adopting network segmentation and role-based access controls (RBAC) can limit the ability of ransomware to move laterally
- Improved incident response: IAM solutions provide detailed logs and audit trails of user activities, which can aid in post-incident analysis and response to ransomware attacks. This information also helps security teams understand the scope of the attack and implement appropriate remediation measures
- Limiting data exposure: Sensitive information is less likely to be compromised by ransomware if the principle of least privilege is strictly enforced and access rights are reviewed often.
5. Backup and Disaster Recovery
Companies can mitigate the impact of ransomware attacks, protect critical data, and keep operations operating smoothly if they have a backup and disaster recovery strategy in place. Recent backups should be accessible so that in the event of a ransomware outbreak, the company can simply and swiftly restore all systems and data to a known, clean state.
Organizations can consider offsite and offline backups to enhance their resilience against attacks. While offsite storage ensures that backups are physically separate from the primary network, offline backups are stored in a disconnected or isolated environment that is not accessible through the network or connected to the primary systems.
6. Vulnerability Management
Vulnerability management is a proactive approach to preventing ransomware attacks by identifying and addressing vulnerabilities in an organization's systems and software regularly. It involves the following activities:
- Vulnerability scanning and assessment: using automated vulnerability scanning tools that assess networks, servers, and endpoints for known vulnerabilities can detect vulnerabilities in a timely manner and prioritize remediation efforts.
- Patch and vulnerability remediation: Once vulnerabilities are identified, patch management will promptly apply security patches and updates provided by IT service providers to fix identified vulnerabilities. It also includes implementing remediation actions, such as modifying configurations, updating software versions, or implementing compensating controls.
- Ongoing monitoring and risk management: Keeping tabs on possible vulnerabilities allows organizations to act swiftly when threats are discovered. Moreover, organizations can assess vulnerabilities based on their severity, potential impact, and likelihood of exploitation to effectively allocate their resources to address the most critical vulnerabilities first.
Learn more: Strengthening IT Compliance: How Vulnerability Management Secures Your Business
7. Incident Response Plan
Beyond preventative measures, it's vital for businesses to have a robust incident response plan in place. This plan would dictate what steps to follow in the event of an attack, who is responsible for what, and how communication both internally and externally will be handled. Having such a plan can significantly reduce the impact and downtime caused by an attack.
8. Engage with Managed Security Service Providers (MSSPs)
For many small to medium-sized enterprises, having an in-house security team might not be feasible. Engaging with an MSSP can be a cost-effective way of benefiting from top-tier security experts who monitor and manage security on a 24/7 basis. MSSPs can also assist with timely patching, threat intelligence, and incident response.
The best way for businesses to avoid and deal with ransomware attacks is to learn how they operate and put into practice robust cybersecurity measures. By using a mix of technological solutions, employee education, and proactive risk management. Organizations may protect themselves against ransomware attacks and limit the extent of the harm they might do. With years of experience in the cybersecurity industry, Adnovum can design and implement cybersecurity resilience services tailored to your specific business demands, ensuring your organization stays ahead of cyberattacks.
📩 Sign up for our newsletter and gain access to exclusive executive insights and event invitations.
Reference:
1. Cybersecurity Ventures. 2023. Who’s Who In Ransomware
2. Cybersecurity Ventures. 2022. Ransomware Market Report.





